- Home
-
Divisions
Energy Systems Division
- Grid Modernization and Security
- Energy Conversion
- Geothermal Materials
Energy Storage Division
- In-situ and Operando Analysis
- Vehicle Technologies
- Grid-level Storage
- Center for Mesoscale Transport Properties
- Long Island Solar Farm
- NSERC
- People
- Org Chart

Energy Systems Division
Renewables and Grid Modernization
Grid Cybersecurity Research
Brookhaven Lab supports grid cybersecurity research for the Department of Energy Office of Cybersecurity, Energy Security and Emergency Response (CESER) and other DOE Offices through the following projects.
AIERCI Tool to Ensure Uninterrupted Energy Flow from Cyber Attacks Targeting Essential Forecasting Data for Grid Operations (2016 – 2021)
Funded by the DOE Cybersecurity for Energy Delivery Systems (CEDS) Program in the Office of Cybersecurity, Energy Security, and Emergency Response (CESER)
Project Team
- Brookhaven National Laboratory (BNL)
- Idaho National Laboratory (INL)
- Argonne National Laboratory (ANL)
- University of North Carolina at Charlotte (UNC Charlotte)
- University of Connecticut (UConn)
- Orange and Rockland Utility (ORU)
Industrial Advisory Board
- Orange and Rockland Utilities (ORU)
- ISO New England
- Electric Power Research Institute (EPRI)
- Statistical Analysis Systems (SAS)
Objective
The objective of this project was to design, develop, and demonstrate the Assess the Impact and Evaluate the Response to Cybersecurity Issues (AIERCI) tool which is needed by utilities. This online tool can assess the impact and evaluate the response to a cyber threat on forecasting data used to operate energy delivery systems by 1) detecting and mitigating anomalies caused by cyberattacks targeting essential forecasting data for loads and renewables, 2) providing a cyber resilient forecasting scheme, and 3) evaluating the impact of cyberattacks targeting forecasting data on grid scheduling functions and operation. In addition, the tool accounts for the impacts of compromised distributed energy resources (DERs) on the transmission network in terms of both forecasting and dynamic security assessment.
Approach
The methodology used to develop this tool consists of cyber issue identification, evaluation of possible responses on the operational forecasting using mathematical models and tools, and determination of the outcome of the response. The overall technical approach, which is illustrated in the figure below, includes the following elements:
- identifies types of data sets, sources, the communication standards, protocols, and media, and storage for such data required by the forecasting models for operational planning or operation
- understands and identifies the potential vulnerability, exploit potential, and exposure in data flows between forecasting input and grid operation
- identifies the potential means for compromising the forecasting input and output data
- propagates the cyberattack by feeding the tampered data to the forecasting model(s) and/or the scheduling functionalities for grid operation and determining the impacts or consequences on the grid operation, or the risk measures.
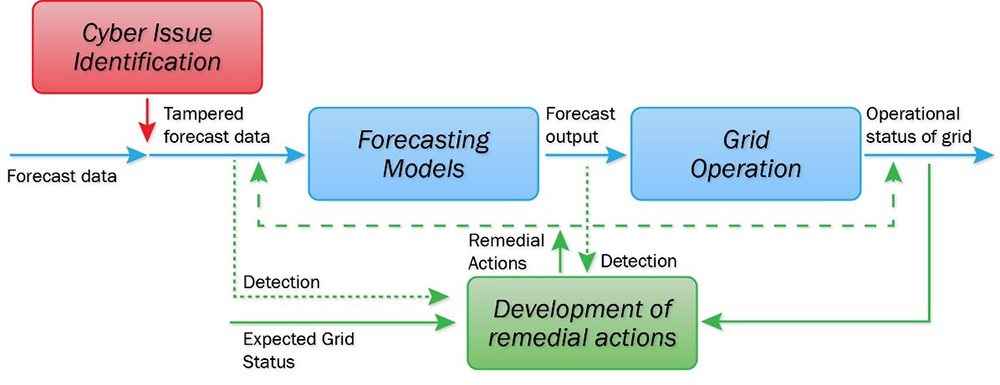
Technical Approach for AIERCI Tool.
Achievements
- Anomaly detection and mitigation (AD&M) module: The AD&M module is based on integrated model- and data analytics-based methods (MBM and DABM) for anomaly detection and mitigation (AD&M) in input data such as load and weather for forecasting functions. The developed AD&M methods have been demonstrated to be highly effective in detecting and mitigating input data anomalies.
- Ensemble Approach (EA) module: The EA module includes adversarial machine learning (AML) and adaptive robust regression (ARR) that are used for a cybersecure load forecasting scheme. Different forecasting schemes may have different strengths and different sensitivities to corrupted or compromised input data.
- Impact Assessment of Scheduling Functions (IASF) module: The IASF module evaluates scheduling functions of different time scales, including day-ahead unit commitment, real-time economic dispatch, and load frequency control to measure the impacts of cyberattacks and the performance of detection and mitigation strategies on grid operation.
The MBM and the weather data related anomaly detection tools have been adopted by a generation and transmission electric cooperative.
An online AIERCI tool that implements these three functional modules has been developed. To ensure the security of the AIERCI tool itself, it was developed by adopting a “security-by-design” approach. AIERCI tool is hosted in a GitHub repository. Access can be obtained by contacting Meng Yue.
Publications
Peer Review: Assess the Impact and Evaluate the Response to Cybersecurity Issues (AIERCI) https://www.energy.gov/sites/default/files/2018/12/f58/BNL%20-%20AIERCI.PDF
Fact Sheet: Assess the Impact and Evaluate the Response to Cybersecurity Issues (AIERCI)
https://www.energy.gov/sites/default/files/2021-04/AIERCI%20-%20BNL.pdf
J. Jiao et al, “Cyberattack-Resilient Load Forecasting with Adaptive Robust Regression,” accepted by the Journal of International Forecasting, to appear.
M. Sobhani, T. Hong, and C. Martin, “Temperature anomaly detection for electric load forecasting”, International Journal of Forecasting 36 (2020) 324–333, abstract available at https://www.sciencedirect.com/science/article/abs/pii/S0169207019301633 .
Z Tang, J. Jiao, P. Zhang, M. Yue, C. Chen, and J. Yan, “Enabling Cyberattack-Resilient Load Forecasting through Adversarial Machine Learning,” IEEE PES General Meeting, August 2019, available at https://arxiv.org/pdf/2001.02289.pdf .
J. Jiao, Z Tang, P. Zhang, M. Yue, C. Chen, and J. Yan, “Ensuring Cyberattack-Resilient Load Forecasting with A Robust Statistical Method,” IEEE PES General Meeting, August 2019, abstract and full paper available at https://ieeexplore.ieee.org/document/8973804 .
M. Cui, J. Wang, and M. Yue, “Machine Learning Based Anomaly Detection for Load Forecasting under Cyberattacks,” IEEE Transactions on Smart Grid, Vol. 10, No 5, January 2019, available at https://www.osti.gov/servlets/purl/1574423 .
M. Yue, T. Hong, and J. Wang, “Data Analytics Based Anomaly Detection in Time Series Data for Online Cybersecure Load Forecasting,” IEEE Transactions on Smart Grid, Vol. 9, No. 6, November 2018, available at https://www.osti.gov/pages/servlets/purl/1601349.
M. Yue, “Evaluation of A Data Analytic Based Anomaly Detection Method for Load Forecasting Data,” IEEE PES General Meeting, July 2018, abstract and full paper available at https://ieeexplore.ieee.org/document/8586608 .
J. Luo, T. Hong, and M. Yue, “Real-time anomaly detection for very short-term load forecasting,” Journal of Modern Power Systems and Clean Energy, vol.6, no.2, pp. 235-243, Mar. 2018, available at https://link.springer.com/content/pdf/10.1007/s40565-017-0351-7.pdf.
M. Yue, “An integrated anomaly detection method for load forecasting data under cyberattacks,” IEEE PES General Meeting, Chicago, July 2017, abstract and full paper available at https://ieeexplore.ieee.org/abstract/document/8273964 .
Annual reports (2016 – 2020) for AIERCI project are also available upon request.
Deep Learning Malware (2020 – 2023)
Funded by multiple DOE Offices and coordinated by the Grid Modernization Laboratory Consortium (GMLC).
Project Team
- Idaho National Laboratory (INL, lead)
- Brookhaven National Laboratory (BNL)
- Lawrence Livermore National Laboratory (LLNL)
- New York Power Authority (NYPA)
- Southern California Edison
- Splunk Inc.
Objective
Once malware is released, other adversaries can repurpose it for their own intentions. The threat evolves and the code remains. Malware is not characterized for the energy sector domains. Pattern matching is static and void after slight changes. Source code for malware is rare requiring lengthy binary analysis and reverse engineering (RE) processing. Malware impacts all applications in the bulk electric system. The objective of this project is to
- Develop malware indicators based on code-behavior for 3 energy domains
- Better understand structured threat: Visual, Sharable, Actionable, and Implementable (IT/OT)
- Resolve all Possible Paths/Constraints for the Malware in days, not years
- Use recent machine learning (ML) concepts to characterize malware for more robust detection based on malware code-behavior, described in a structured threat for energy sector domains.
Tools Developed
ESE (Enhanced STIX Elevation) tool
Publications
T. Zhao, B. Beckman, M. Yue, and R. Foster, “ESE: A Tool for Enhanced STIX Elevation,” Resilience Week, September 2022.
-

Meng Yue
Group Leader, Research Staff Electrical Engineer
Energy Systems Division
Interdisciplinary Science Department
(631) 344-7140, yuemeng@bnl.gov




